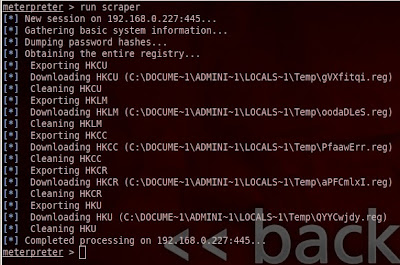
We will start to navigate Linux security from zero
how to protect your system from unauthorized users, and how to monitoring your Linux system (demons, ports, processes and services installed on your machine)
First
Read log Files
when i log-in to my system i have to read two important files (boot.log and dmesg.log)
These files show me boot sequence and booting hardware such as hard disk and network adapter ,and if there any problem in booting operation.
log files located in /var/log
reading dmesg file by command
cat /var/log/dmesg
? so what to check in this file
- check kernel version and compare it with your kernel version
when you look at dmesg file you will see something like that (Linux version 2.6.32-5-686 Debian 2.6.32-31)
and by comparing it with your kernel number from command uname -a and output will be (Linux rsht 2.6.32-5-686 )
so it's the same version of kernel
- check your memory and CPU from dmesg file and compare it with your resources
Common Linux log files name and usage
/var/log/message: General message and system related stuff
/var/log/auth.log: Authenication logs
/var/log/kern.log: Kernel logs
/var/log/cron.log: Crond logs (cron job)
/var/log/maillog: Mail server logs
/var/log/qmail/ : Qmail log directory (more files inside this directory)
/var/log/httpd/: Apache access and error logs directory
/var/log/lighttpd: Lighttpd access and error logs directory
/var/log/boot.log : System boot log
/var/log/mysqld.log: MySQL database server log file
/var/log/secure: Authentication log
/var/log/utmp or /var/log/wtmp : Login records file
/var/log/yum.log : Yum log files
/var/log/message: General message and system related stuff
/var/log/auth.log: Authenication logs
/var/log/kern.log: Kernel logs
/var/log/cron.log: Crond logs (cron job)
/var/log/maillog: Mail server logs
/var/log/qmail/ : Qmail log directory (more files inside this directory)
/var/log/httpd/: Apache access and error logs directory
/var/log/lighttpd: Lighttpd access and error logs directory
/var/log/boot.log : System boot log
/var/log/mysqld.log: MySQL database server log file
/var/log/secure: Authentication log
/var/log/utmp or /var/log/wtmp : Login records file
/var/log/yum.log : Yum log files
second
check your mounted driver by using command
df -h
now
Let's start with securing,
booting of Linux is passing through many levels or stages
Bios---->grub boot---->kernel(initializes hardware)----->init
init is the first program run after kernel it do the following:
1- Start up system run level
2- Specify processes to be executed during system boot
3- Specify processes to be run when the specified run-level is entered
4- Specify processes to be run on certain run-levels with actions like respawn so the process is restarted any time it terminates
5- Specify certain actions or processes to be run if certain signals or user actions are indicated
These program read and apply configuration from /etc/inittab
for more information (http://linux.die.net/man/8/init or by command man 8 init)
when we look at it's configuration file (/etc/inittab) it's look like
# Author: Miquel van Smoorenburg,
# Modified for RHS Linux by Marc Ewing and Donnie Barnes
id:3:initdefault:
# System initialization.
si::sysinit:/etc/rc.d/rc.sysinit
l0:0:wait:/etc/rc.d/rc 0
l1:1:wait:/etc/rc.d/rc 1
l2:2:wait:/etc/rc.d/rc 2
l3:3:wait:/etc/rc.d/rc 3
l4:4:wait:/etc/rc.d/rc 4
l5:5:wait:/etc/rc.d/rc 5
l6:6:wait:/etc/rc.d/rc 6
# Things to run in every runlevel.
ud::once:/sbin/update
# Trap CTRL-ALT-DELETE
ca::ctrlaltdel:/sbin/shutdown -t3 -r now
# When our UPS tells us power has failed, schedule a shutdown for 2 minutes from now.
pf::powerfail:/sbin/shutdown -f -h+2 "Power Failure; System Shutting Down"
# If power was restored before the shutdown kicked in, cancel it.
pr:12345:powerokwait:/sbin/shutdown -c "Power Restored; Shutdown Canceled"
# Run gettys in standard runlevels
1:2345:respawn:/sbin/mingetty tty1
2:2345:respawn:/sbin/mingetty tty2
3:2345:respawn:/sbin/mingetty tty3
4:2345:respawn:/sbin/mingetty tty4
5:2345:respawn:/sbin/mingetty tty5
6:2345:respawn:/sbin/mingetty tty6
# Run xdm in runlevel 5
x:5:respawn:/etc/X11/prefdm -nodaemon
now we have to do the following:
1- reduce number of TTYs it's ,take resources (by putting # before every TTY)
just leave in that you may need it in emergency
1:2345:respawn:/sbin/getty 38400 tty1
#2:23:respawn:/sbin/getty 38400 tty2
#3:23:respawn:/sbin/getty 38400 tty3
#4:23:respawn:/sbin/getty 38400 tty4
#5:23:respawn:/sbin/getty 38400 tty5
#6:23:respawn:/sbin/getty 38400 tty6
2- defualt run-level from 3 to 5 (usefewer resources and graphical TCP X windows)
3- Disable ctl+alt+delete
(by putting # before ca:12345:ctrlaltdel:/sbin/shutdown -t1-a -r now)
# What to do when CTRL-ALT-DEL is
pressed.
#ca:12345:ctrlaltdel:/sbin/shutdown -t1-a -r now
Now we have to change some files to hide information about my OS ,it's called (banner implementation)
There are more options to encrypt your boot operation
1- use strong password on bios
2- encrypt your grub file by using command grub-md5-crypt,
for more information (man grub-md5-crypt)
3- use a very strong password for root
4- don't access to the system by root or privileged user
use command cat /etc/issue will print information about your OS such as (Debian GNU/Linux 6.0 \n \l)
and cat /etc/motd also will print important information about your OS, so now we have to change information in these files to hide these information by editing it with any you want.
The different between issue and motd is issue print it's value before you log-in and motd after you log-in
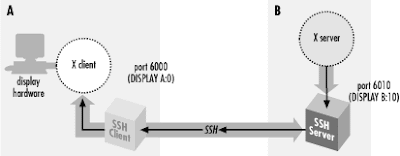
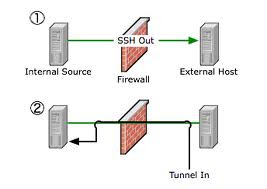
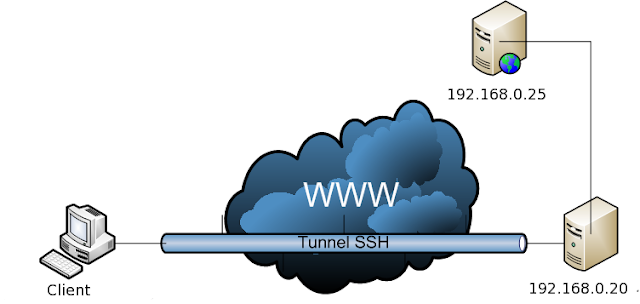
we must disable root to access via ssh by editing it's configuration file
(/etc/ssh/sshd_config)by set permit root log-on to no